:quality(75)/cloudfront-us-east-1.images.arcpublishing.com/elcomercio/YJ3GHY5M6BGKNGWDEVEWQ57NII.png)
Microsoft has confirmed the theft of source code for some of the technology company’s services, which the group of cybercriminals calling itself LAPSUS$ claimed a few days ago and shared via Telegram, after managing to compromise one of the company’s accounts. .
YOU CAN SEE: Microsoft | LAPSUS$ hacker group claims to have stolen source code for Bing, Bing Maps and Cortana
Last Sunday, LAPSUS$ published a screenshot through this messaging application in which it claimed to have accessed Microsoft repositories by hacking an Azure DevOps server, a set of tools for developers.
Then, the group of hackers claimed to have stolen 90 percent of the data from Bing Maps and 45 percent of the data belonging to Microsoft’s search engine, Bing, and its Assistant, Cortana.
YOU CAN SEE: Zelda: Ocarina of Time, Minesweeper and Resident Evil are the candidates to enter the Gaming Hall of Fame
This data leak occurred after this same group of cybercriminals claimed responsibility for the theft of several electronic signature certificates from Nvidia developers and internal information from Samsung.
In recent days, Microsoft has observed activity that has been attributed to the LAPSUS$ group, which the company tracks as DEV-0537, and which is known for using “an extortion and destruction model without deploying ‘ransomware’ payloads,” as indicated in a statement.
YOU CAN SEE: Microsoft launches DirectStorage on PC to improve the loading speed of video games
After investigating the attack, the software developer has reported that “no client code or data was involved in the activities observed” and carried out by DEV-0537.
Thus, it has determined that only one of its accounts has been compromised and that its security teams were able to limit the attack to prevent further activity by cybercriminals.
And it has downplayed source code theft. “Microsoft does not rely on code secrecy as a security measure, and viewing source code does not lead to increased risk,” he said in the statement.
In addition, it has clarified that the team in charge of protecting the security of its data was already investigating the compromised account “based on threat intelligence” when LAPSUS$ publicly revealed its intrusion through Telegram.
THE RAPID EXPANSION OF LAPSUS$
On the other hand, Microsoft has explained what has been the journey that this group has had, which began to attack organizations in the United Kingdom and South America to expand later, as well as some of its “global objectives”.
Among these targets are “including organizations in the government, technology, telecommunications, media, retail and healthcare sectors.”
However, it has insisted that DEV-0537 has also attacked anonymous users on cryptocurrency exchanges and has mentioned some of the methods it uses to break into these devices.
Among them, those that include phone-based social engineering, SIM swapping to facilitate account acquisition, access to personal emails or pay suppliers and business partners of the target organizations to access credentials and authentication approval stand out. multifactorial (MFA).
In your case, the Microsoft Threat Intelligence Center (MSTIC) has determined that DEV-0537’s goal is to access your data through stolen credentials and that it is an “actor motivated by theft and destruction ”.
Likewise, it has pointed out that the tactics, techniques and procedures (TTP) of this group “constantly change and evolve”, it has detected a series of parameters in its behavior to compromise the identities of the users and obtain free access to the different organizations susceptible to be attacked.
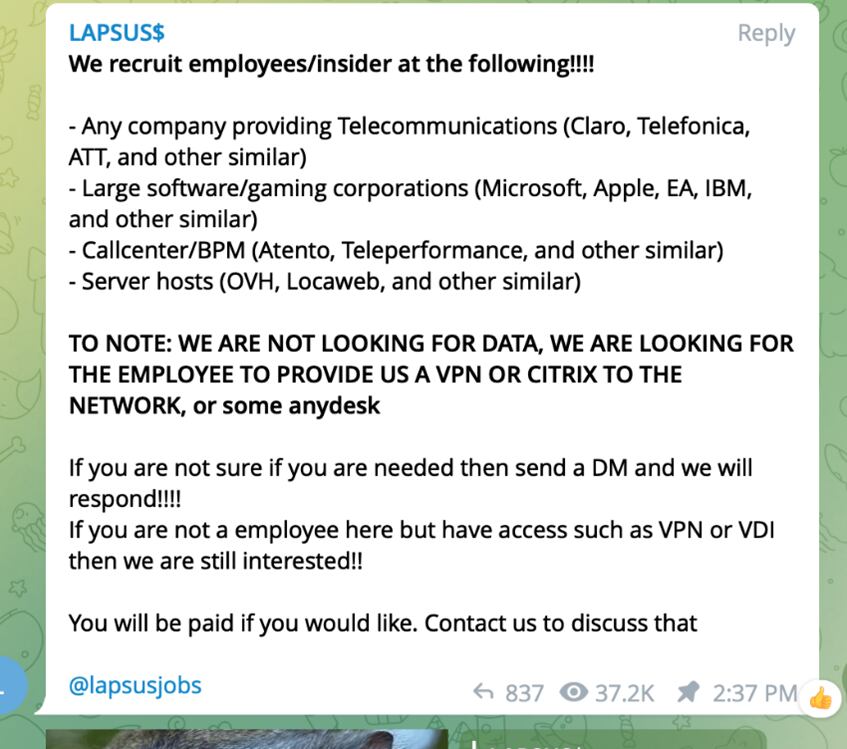
These methods include implementation of the Redline password stealer, buying credentials and tokens on illegal forums, paying employees of target organizations and their MFA approval, as well as searching public code repositories for exposed passwords.
Once these credentials are stolen, DEV-0537 accesses systems and applications that typically include a virtual private network (VPN), virtual desktop infrastructure (VDI), such as Citrix, or identity providers (including Azure Active Directory and Okta).
For organizations using MFA security, DEV-0537 has previously used two techniques to circumvent their security system: replaying session tokens and using stolen passwords.
Through this theft, it has been able to activate the sending of MFA notices so that legitimate users of the compromised accounts, unaware of the manipulation of this authentication system, grant the necessary authorization.
In some cases, LAPSUS$ has accessed victims’ personal accounts and prompted them to enter additional credentials that could be used to access corporate systems or their professional accounts.
Since employees generally use these personal accounts as a second factor for authentication or recovery of their passwords, the group of attackers has used these accesses to reset them and complete the account recovery system with other new credentials.
Another common method used by cybercriminals is to bribe an organization’s employees, vendors, or business partners who, for a fee, provide their credentials and pass multi-factor authentication.
Likewise, it has also offered them the option of downloading and installing remote control applications on their computers, such as AnyDesk, which would allow them to control the system.
In another of the observed attacks, Microsoft has highlighted that DEV-0537 actors performed a SIM swapping attack to access a user’s phone number before logging into their work or corporate network.

This method allows actors to handle the phone authentication requests they need to gain access to an organization. Therefore, once the standard user credentials or access were obtained, the attackers were able to access the VPN system of these organizations.
To circumvent security systems, in some cases, DEV-0537 joined its system to the cloud-based identity and access management service, Azure Active Directory (Azure AD) of the attacked corporations.
Finally, Microsoft has highlighted that, in its investigations, it has verified that LAPSUS$ uses AD Explorer, a free and freely accessible tool, in the majority of its attacks.
It is an indicator that allows viewing, editing and browsing the databases, which the cybercriminals would have used to enumerate and recognize each of the users of the attacked networks.
Thanks to it, they can understand which are the accounts that have the greatest privileges, such as those of the directors or administrators of these companies.
In addition, they proceeded to search for collaboration platforms like SharePoint or Confluence, issue tracking solutions like JIRA, code repositories like GitLab and GitHub, and organization collaboration channels like Teams or Slack to discover more credentials and data to access sensitive information. .
- Microsoft | LAPSUS$ hacker group claims to have stolen source code for Bing, Bing Maps and Cortana
- Zelda: Ocarina of Time, Minesweeper and Resident Evil are the candidates to enter the Gaming Hall of Fame
- Microsoft launches DirectStorage on PC to improve the loading speed of video games
- Bill Gates: what are the four things that the creator of Microsoft needs to be happy?
- Devices from Apple, Microsoft and Google are the hardest to repair, report says
Source: Elcomercio





